Lessons in LinkedIn Password Cracking
 Tuesday, June 12, 2012 at 10:17AM
Tuesday, June 12, 2012 at 10:17AM So this past week the password cracking community had some excitement. Several dumps of hashes were leaked. One of those was LinkedIN. This caught my eye since most professionals use this social media service. I am a fan of passwords ever since I met Matt Weir when he presented about the science of password cracking. One of his talking points was that people can pick anything as passwords but generally follow a pattern. How many of us have a capital first letter and end with the number 1? Password1 is technically a strong password in the eyes of Active Directory.
A few months ago, digininja created a tool Pipal which allows analysis of passwords. This allowed the community a common metric and analysis tool to run the various password dumps. Using the various data from previous dumps, I was able to fine tune my hashcat rules to be able to crack over half the LinkedIn hashes.
Lessons Learned
- Start with a good dictionary. KoreLogic has a group of amazing word lists here. In addition, SkullSecurity has a list of previously cracked passwords and various wordlists which I also added to my master_wordlist.dic. To make my master_wordlist.dic I would "cat infile >> master_wordlist.dic". Make sure to use the double >> or else you wipe over the words already in the master_wordlist.dic.
- After adding everything to your list, you need to sort and remove the duplicates. In Windows it is a pain since your list is too big for Excel and Access just plain stinks to use. Score 1 for Bash! The command "sort master_wordlist.dic | uniq > master_sorted_wordlist.dic" worked perfectly.
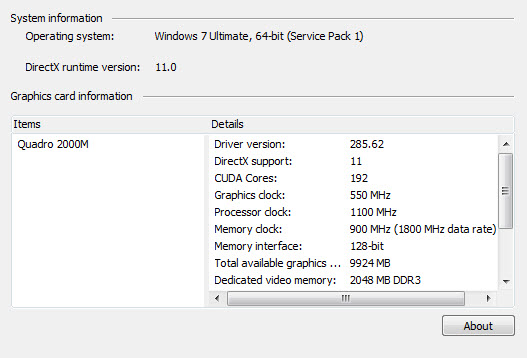
- Fire up hashcat and crack! Don't forget to use some rules and masks! You don't need a GPU but it helps. One thing I learned was my Dell Laptop has a nVidia card so check your gear.
- Now that I have a cracked list in the hash:plaintext format we need to remove the hash part. Score 2 for Bash! The command "grep -o '[^:]*$' infile > outfile" will remove the hashes leaving you a file with only plaintext passwords.
- At this point you can perform a Pipal analysis or you can run your list through hashcat again using the cracked passwords as your new dictionary and apply the rules and masks.
You can find the Pipal Analysis of the LinkedIn dump here. Happy Cracking!