Using Metasploit to remove Malware
 Friday, March 11, 2011 at 12:16PM
Friday, March 11, 2011 at 12:16PM So I have a family member who loves malware however it is not like us who like to research and understand it. He likes to goto websites ("I never went to that site.") and click every link possible as fast as he can.
As a result, he has a great collection of malware.
He has gotten every version of FakeAV known. Here is how I use Metasploit to remove it.
Step 1: Generate a windows meterpreter executable and rename it "explorer.exe". Most malware do not allow any AV or Malwarebytes to run. Renaming the file "explorer.exe" will allow it to get through on the malware's whitelist.
Step 2: Run our executable on the infected machine and connect back/bind to the meterpreter session. Since Meterpreter does not touch disk and injects itself into memory this is a great way to get a foothold onto the machine.
Step 3: Escalate to SYSTEM. Windows 7 is no longer a problem thanks to @Dave_Rel1k and @KevinMitnick UACBypass. I love this script/post exploit module. Go to @Derbycon!
Step 4: Reward yourself... I recommend Crown Royal with a splash of Ginger Ale. YMMV
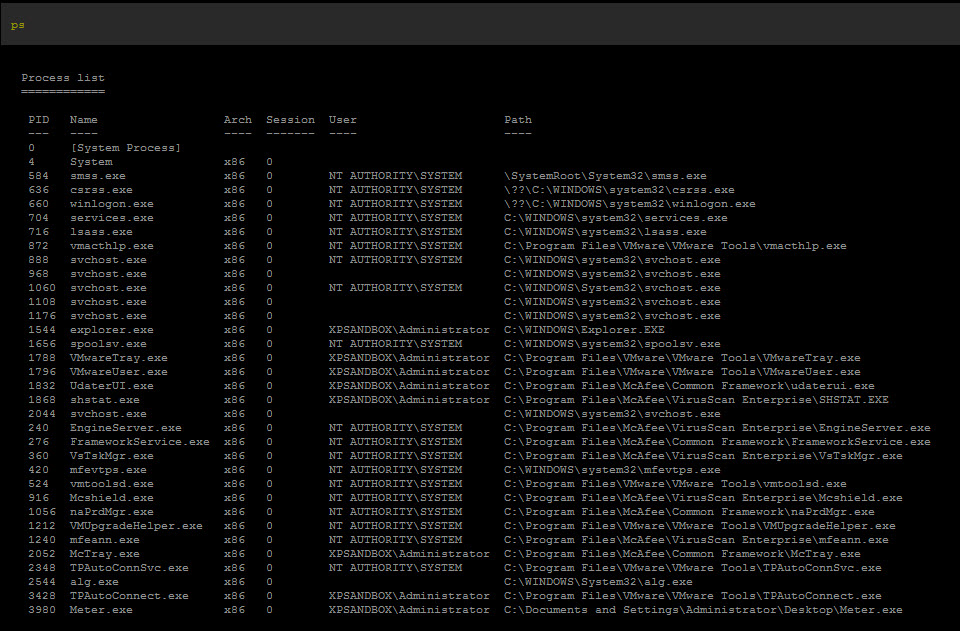
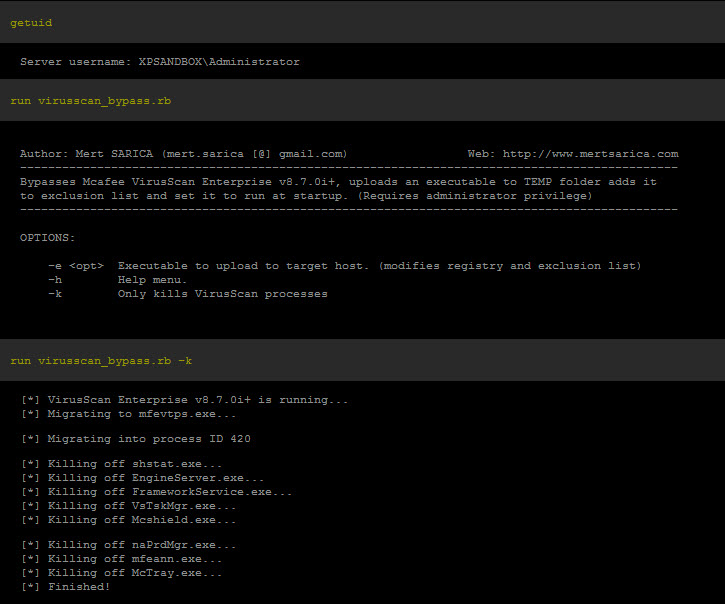
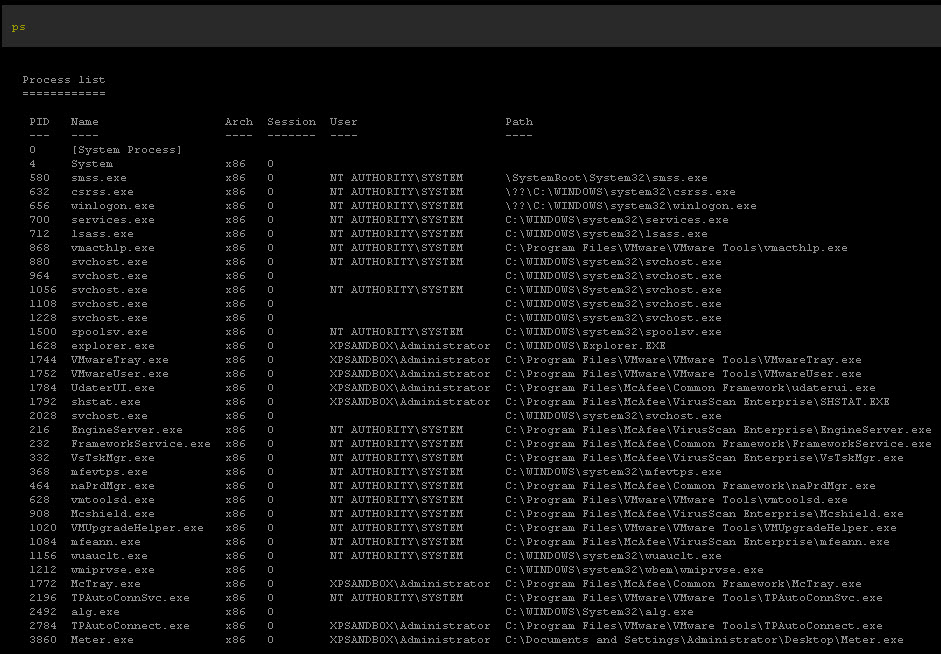
Step 5: Now that you are SYSTEM, type "ps". Some of these things are not like the other. Some of these things just don't belong.
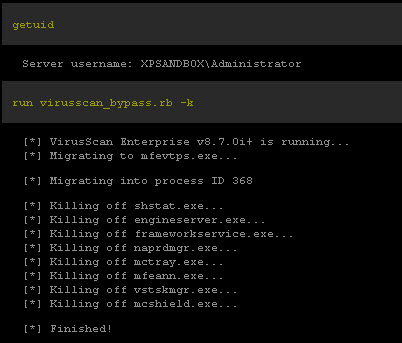
Step 6: Identify the PID number next to the rouge processes and "kill ####"
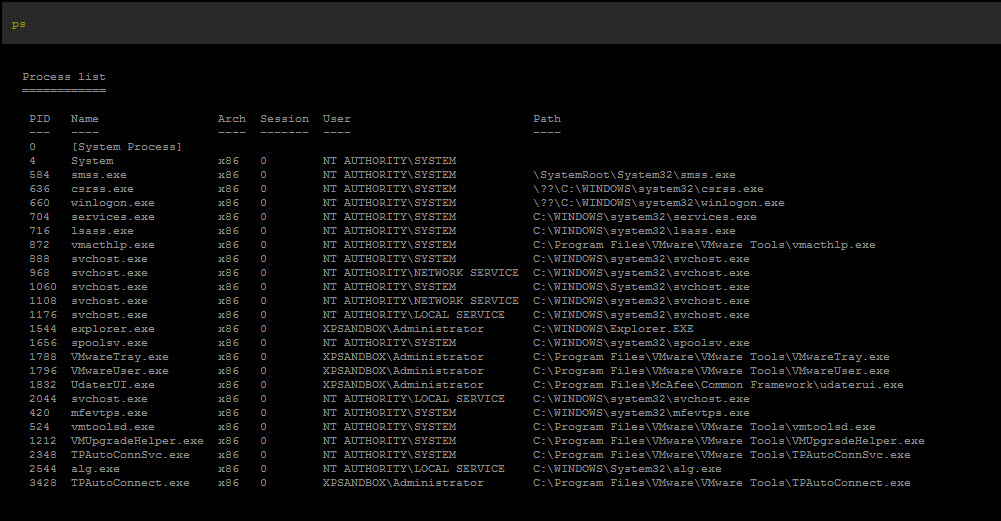
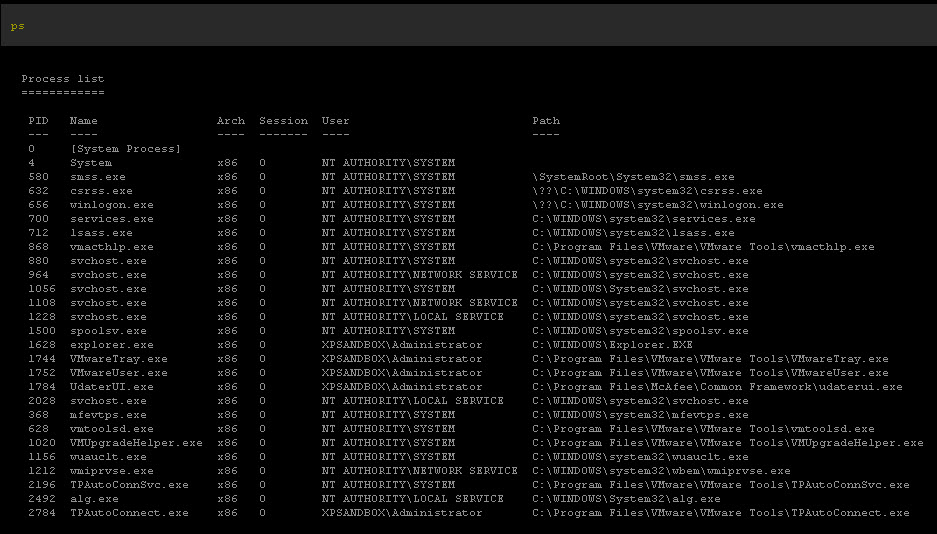
Step 7: At this point, you should have broken the hold on the system that the malware had. Install http://www.malwarebytes.org/mbam-download.php
Step 8: Run some scans and remove the naughty objects. I also recommend something AV/Malware Related... McAfee, Microsoft Security thingy, anything.... Check NSSLabs for some recommendations.
Step 9: Give the computer back to your family member and wait till next week when he finds a new site that he didn't visit and runs a file he never ran!
 McAfee,
McAfee,  Metasploit,
Metasploit,  NSSlabs in
NSSlabs in  Virus/Malware
Virus/Malware